Hacktober 2020 CTF - Prefetch Perfection 2
Oct 16, 2020
Challenge Description
One of the processes loaded a cookie file belonging to cmaldanado, what is the name of the process? Submit the flag as flag{process.exe}.
Use the file from Prefetch Perfection.
Max Attempts: 10
Solution
For this chalange we had to parse .pf prefetch files. we used windowsprefetch for this Task.
We started by prefetching the whole directory.
m3dsec@local:~/hacktoberctf/forensics/05_Prefetch_Perfection$ prefetch.py -d prefetch/
============================
POWERSHELL.EXE-3E7086C1.pf
============================
Executable Name: POWERSHELL.EXE
Run count: 1
Last Executed: 2017-05-03 02:11:31.583520
Volume Information:
Volume Name: \DEVICE\HARDDISKVOLUME1
Creation Date: 2017-04-26 06:17:23.091272
Serial Number: 46ca3ac8
...
\DEVICE\HARDDISKVOLUME1\WINDOWS\WINDOWSSHELL.MANIFEST
\DEVICE\HARDDISKVOLUME1\WINDOWS\SYSTEM32\UXTHEME.DLL
\DEVICE\HARDDISKVOLUME1\WINDOWS\SYSTEM32\DWMAPI.DLL
\DEVICE\HARDDISKVOLUME1\WINDOWS\GLOBALIZATION\SORTING\SORTDEFAULT.NLS
\DEVICE\HARDDISKVOLUME1\WINDOWS\FONTS\STATICCACHE.DAT
12332: \DEVICE\HARDDISKVOLUME1\$MFT
Going through the output, we can see that DLLHOST.EXE is loading some resource from CMALDONADO AppData folder.
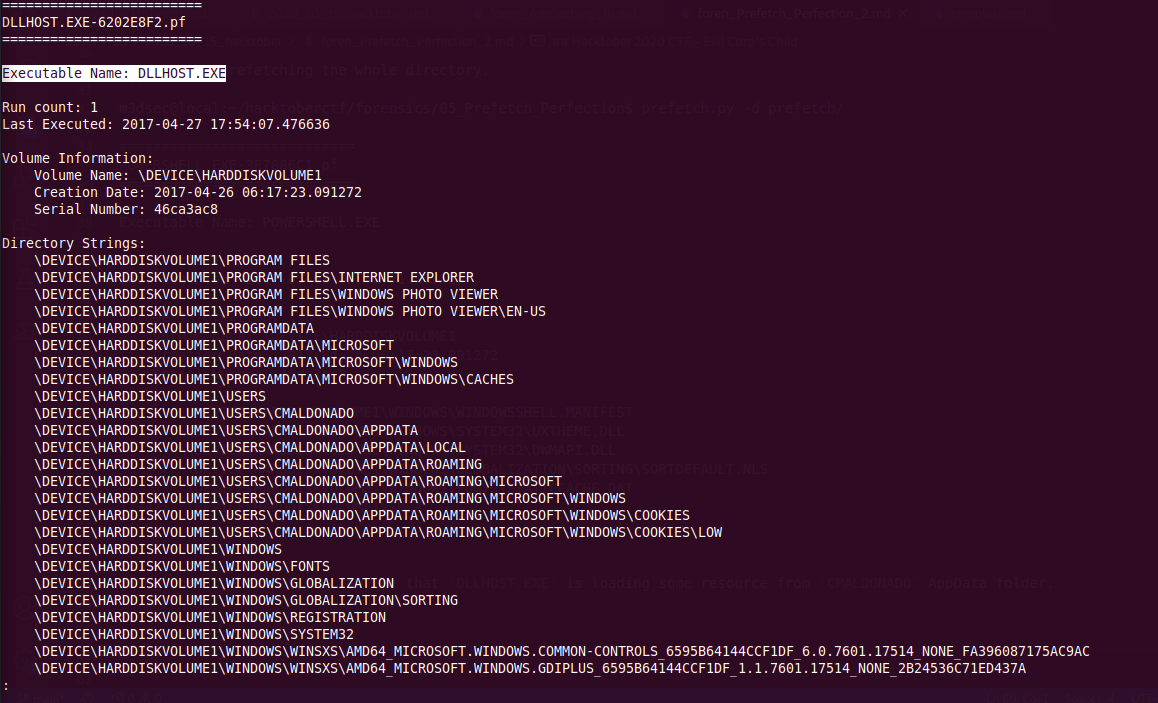
And the Flag was : flag{dllhost.exe}